Is it possible to seamlessly access devices behind firewalls and NAT routers? The increasing reliance on remote access for IoT devices and other applications necessitates robust solutions to overcome the challenges posed by network security measures.
The scenario unfolds: a Fortigate firewall, nestled behind Network Address Translation (NAT), presents a common hurdle. Its Wide Area Network (WAN) interface sports a private IP, subsequently translated by a higher-level network device to a public IP. While the firewall's web interface is accessible via the public IP, configuring an IPsec remote access Virtual Private Network (VPN) and connecting with FortiClient VPN can expose some complexities.
Consider the industrial Internet of Things (IoT). Many applications in this realm require configuration adjustments or yield valuable data. However, the underlying devices often lack accessible operating systems (OS) and are shielded by firewalls, complicating external access.
The world of remote access to IoT devices presents unique challenges and requires innovative solutions. Let's delve into the intricacies of accessing devices behind firewalls and NAT routers.
Consider the use case of accessing a private MQTT broker. This is essential when IoT devices and sensors are deployed remotely at customer sites or in open fields to measure environmental factors. TightVNC, an open-source Virtual Network Computing (VNC) software, provides remote desktop access on IoT devices.
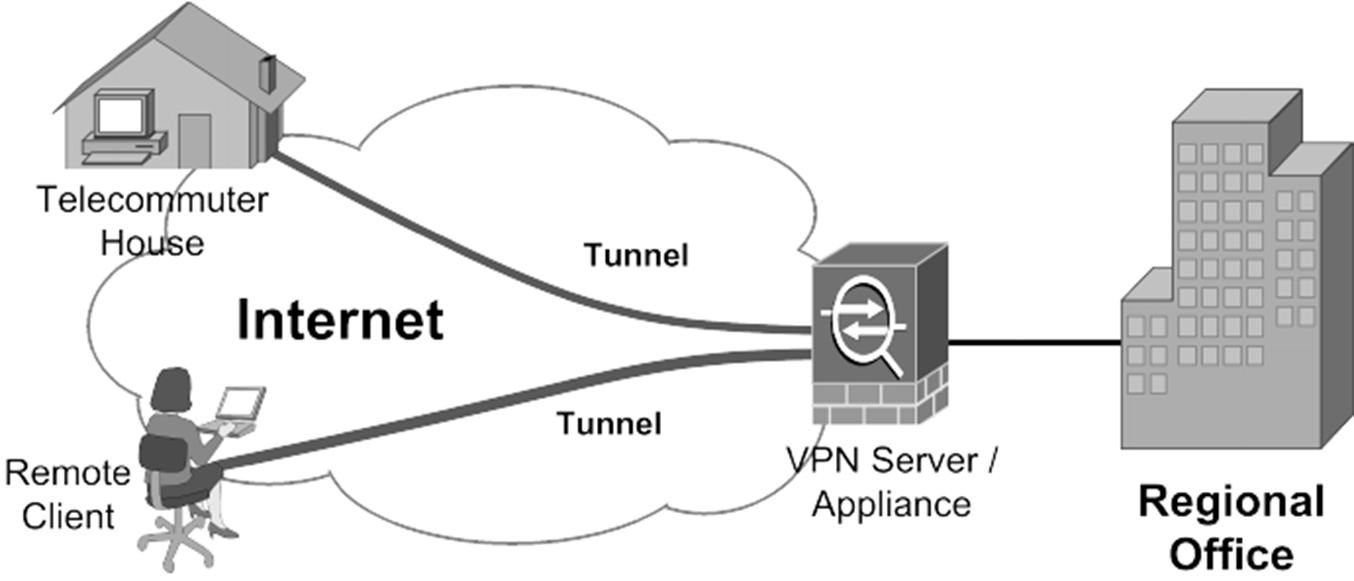
The core function of a firewall is to prevent unauthorized network access. However, a well-managed tunnel should ideally bypass this restriction. It is important to note that the firewall's configuration and how the tunnel is managed are crucial to understand. It might be important to be wary of the administrator of the remote network you are connecting to.
In such situations, the ability to access devices behind NAT routers and firewalls over the internet becomes paramount. The challenge lies in establishing secure connections without direct IP address accessibility.
One potential solution involves using SSH port forwarding to remotely connect to a closed device, such as a web server behind a firewall. This technique enables tunneling application ports from a remote machine through a local device with external SSH access on the same remote network.
SocketXP offers a cloud-based IoT remote access solution, facilitating remote connections to IoT GUI desktops via VNC over the internet. The company's offerings extend to remote management, access, and monitoring of IoT devices, Raspberry Pi fleets, and Linux machines behind NAT routers and firewalls.
Another intriguing possibility arises with Secure Tunneling. This method employs MQTT (Message Queuing Telemetry Transport) to transfer an access token to the device, subsequently utilizing WebSockets to establish an SSH connection through the firewall.
Many IoT devices are deployed behind firewalls or NAT routers, increasing the complexity of establishing and maintaining a secure connection. The objective is to provide access to remote devices without having to discover their IP addresses or modify firewall settings.
This approach enables the direct connection through SSH or VNC to Raspberry Pi devices behind firewalls, offering the illusion of being on the local network.
Since this technique seems to be fairly general, one could imagine generic public services, like a DynDNS, that additionally to the dynamic update of the DNS entries also stores some port mapping that can be queried by devices that want to connect to the service behind the NAT.
It's often acceptable to poke a hole in the firewall for remote access, even if it's infrequent. In cases where opening a port isn't possible, or if you'd rather avoid it, a shell script could monitor an internet-available resource and listen for commands to launch a reverse tunnel.
These methods enable remote access to devices behind firewalls, providing a pathway to devices that are otherwise inaccessible. This simplifies the configuration and reduces troubleshooting time for devices behind firewalls.
The proliferation of devices brings challenges to remote access and management. It starts with a solid understanding of network security principles, followed by the right tools and strategies.
For VPN devices, NAT configuration is necessary if the devices behind the VPN need access to the internet. This allows internet packets to pass through the router.
In a Mikrotik example, a node on 10.5.50.2 is placed, and its port 2500 needs to be reached through the WAN interface of the Mikrotik on port 2500.
One might question if the setup makes sense, especially when no internet access is desired from remote. It's essential to assess the setup's validity and ensure the desired network behavior is achieved.
Remote IoT device connections on macOS and issues with remote access using SSH can be significant problems, particularly behind restrictive corporate firewalls or routers.
The common scenario involves an office PC behind a firewall connected to the internet.
Solutions include port knocking, P2P, VPN, and SSH for remote access to a Linux server behind a firewall. Port knocking involves sending special packets to temporarily open a hole in the firewall.
SSH port forwarding tunnels application ports from a remote machine we don't have direct access to, using a local device with external SSH access.
SSH reverse proxy tunneling offers a secure method to set up remote access to IoT devices behind a NAT router or firewall. It's suitable for various users, from hobbyists to professionals, and enables secure SSL/TLS VPN tunnels.
Learn how to remotely access IoT devices behind a firewall, using methods such as port forwarding, VPN, RDP, and SSH.
The core of remote access lies in understanding the principles of network security and applying the right tools. One such tool is a cloud-based IoT remote access and device management solution that provides SSH access to remotely located IoT devices like Raspberry Pi, Arduino, or any embedded Linux devices behind a NAT router or firewall over the internet using secure SSL/TLS VPN tunnels.
To ensure proper connectivity, it's often necessary to allow NAT for VPN devices. This allows internet packets to pass through the router. In the NAT section, specifically in the IP/Firewall section, one should check for existing rules or add the appropriate ones to enable communication.
To troubleshoot, ping the LAN's default gateway behind the Fortigate and execute a route print to confirm the internal segment is reachable via the VPN pool IP.
The following table provides a concise overview of various methods for remote access. It includes a summary of the access type, a brief description, potential advantages and disadvantages, and suggested use cases.
The table below illustrates the variety of methods that can be used for remote access and their respective characteristics.
| Method | Description | Advantages | Disadvantages | Use Cases |
|---|---|---|---|---|
| Port Forwarding | Allows external traffic on a specific port to be directed to an internal device. | Simple to set up, widely supported. | Requires a fixed IP address or dynamic DNS, potentially less secure if not configured properly. | Accessing a web server, SSH server, or any service that listens on a known port. |
| VPN (Virtual Private Network) | Creates a secure tunnel to a private network, allowing access to multiple resources. | Secure, allows access to multiple resources, flexible. | Requires VPN client software, more complex setup, may have performance overhead. | Accessing an entire network, remote access to internal servers and services. |
| SSH Tunneling | Secure Shell (SSH) can be used to tunnel traffic, providing secure access. | Secure, flexible, can bypass firewalls. | Requires SSH access, requires some understanding of SSH. | Accessing a specific service, bypassing restrictive firewalls. |
| Reverse SSH Tunneling | Allows a device behind a firewall to initiate a connection to an SSH server, creating a tunnel. | Effective for devices behind NAT or firewalls, secure. | Requires an SSH server, more configuration than standard SSH. | Accessing a device behind a firewall without port forwarding. |
| Cloud-Based Solutions (e.g., SocketXP) | Utilizes cloud services to create secure tunnels for remote access. | Simple setup, often no need for port forwarding, managed security. | Reliance on a third-party service, potential costs. | Remote access to IoT devices, accessing devices behind NAT and firewalls. |
| VNC (Virtual Network Computing) | Allows remote graphical access to a device's desktop. | Simple to use for graphical access. | Less secure without encryption, can be bandwidth-intensive. | Remote desktop access, troubleshooting. |
| RDP (Remote Desktop Protocol) | Microsoft's protocol for remote desktop access. | Good performance, integrated into Windows. | Primarily for Windows devices, requires port forwarding or VPN. | Remote desktop access for Windows. |
The table above is a starting point for understanding how remote access is possible. Each method offers unique benefits and drawbacks, and the selection depends on the specific needs of the application and the security requirements.
When configuring IPsec remote access with full tunneling, it is important to check and configure the settings for optimal use.
For additional resources, refer to Fortigate IPsec VPN documentation.